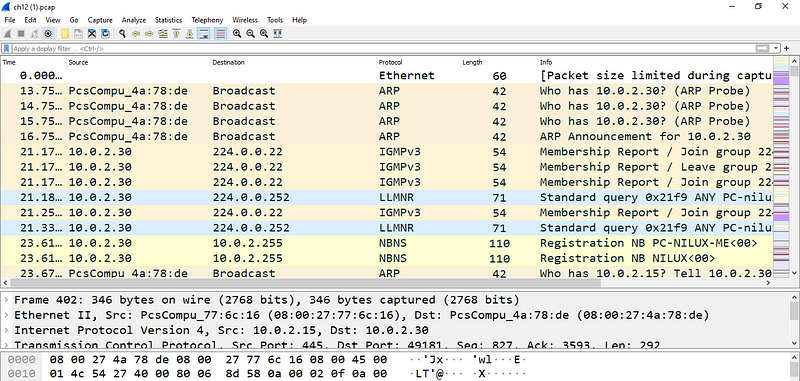
Active Directory User Login History - Audit all Successful and Failed Logon Attempts - Enterprise Network Security Blog from IS Decisions

ADTimeline – Active Directory forensics with replication metadata at the FIRST Technical Colloquium | Agence nationale de la sécurité des systèmes d'information
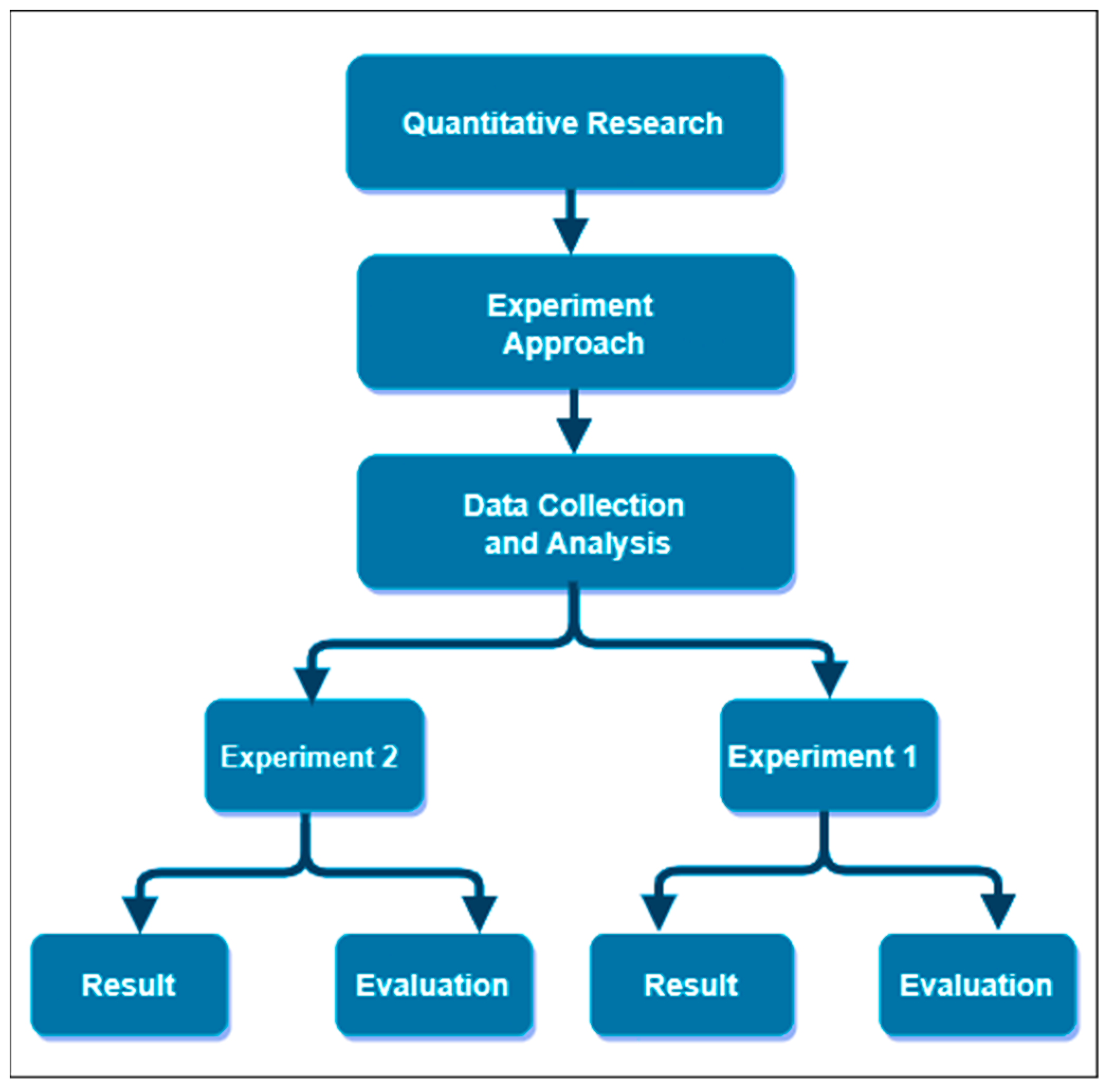
Future Internet | Free Full-Text | Exploiting Misconfiguration Vulnerabilities in Microsoft’s Azure Active Directory for Privilege Escalation Attacks
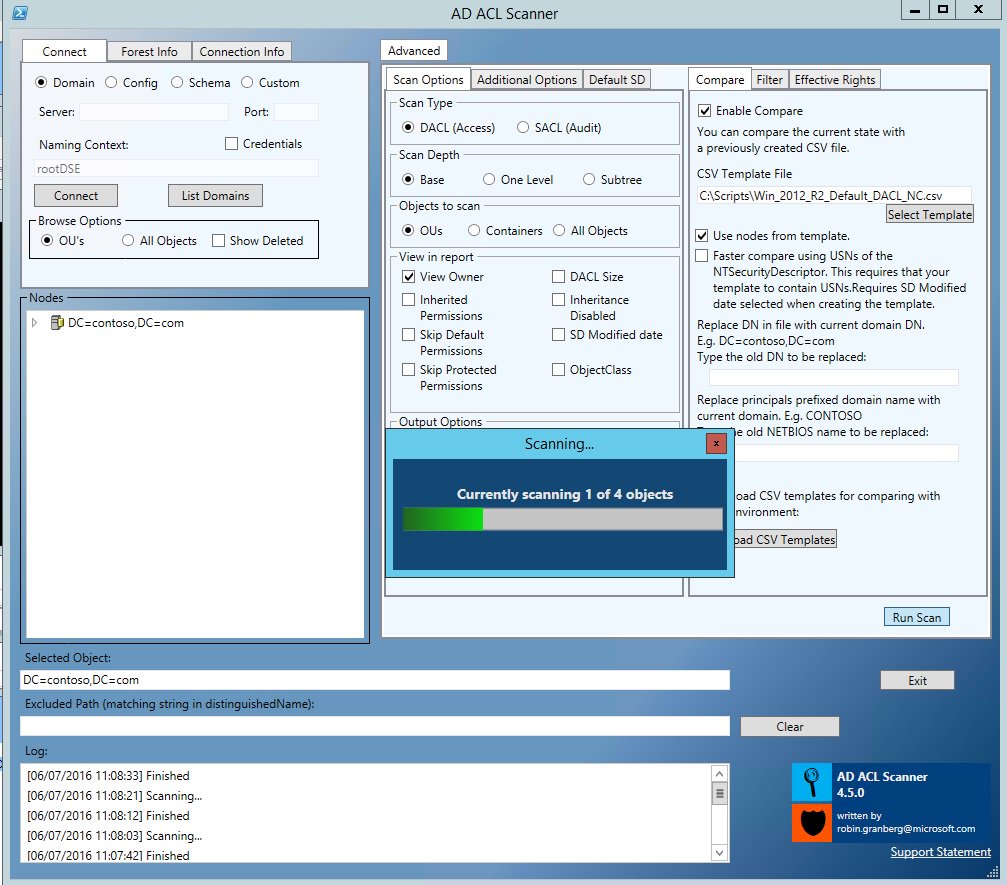
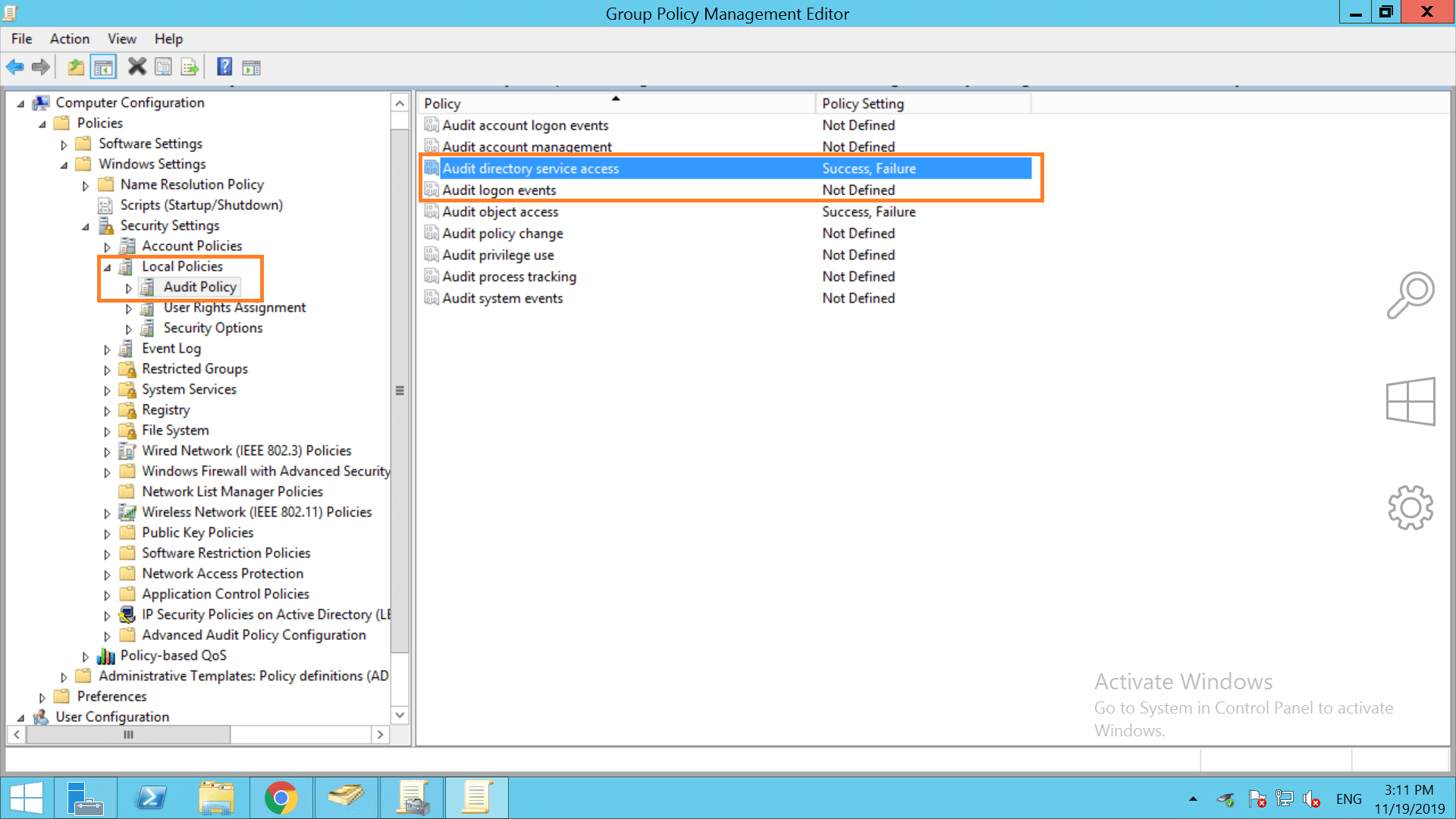
James van den Berg MVP ☁ on Twitter: "Forensics: Active Directory ACL investigation https://t.co/rfFMVRRqwg #AD #Winserv https://t.co/OrW3AEJ9ts" / X
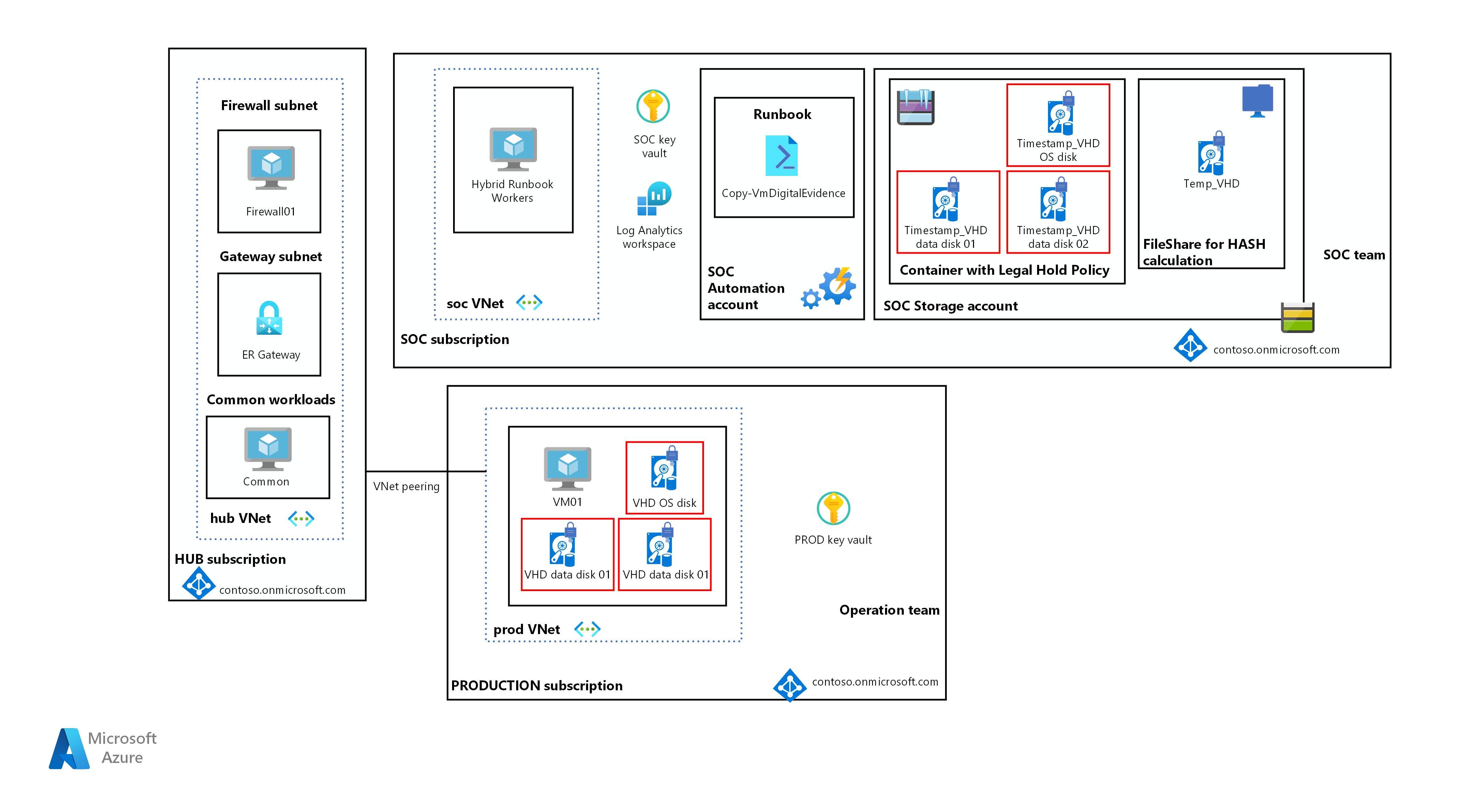
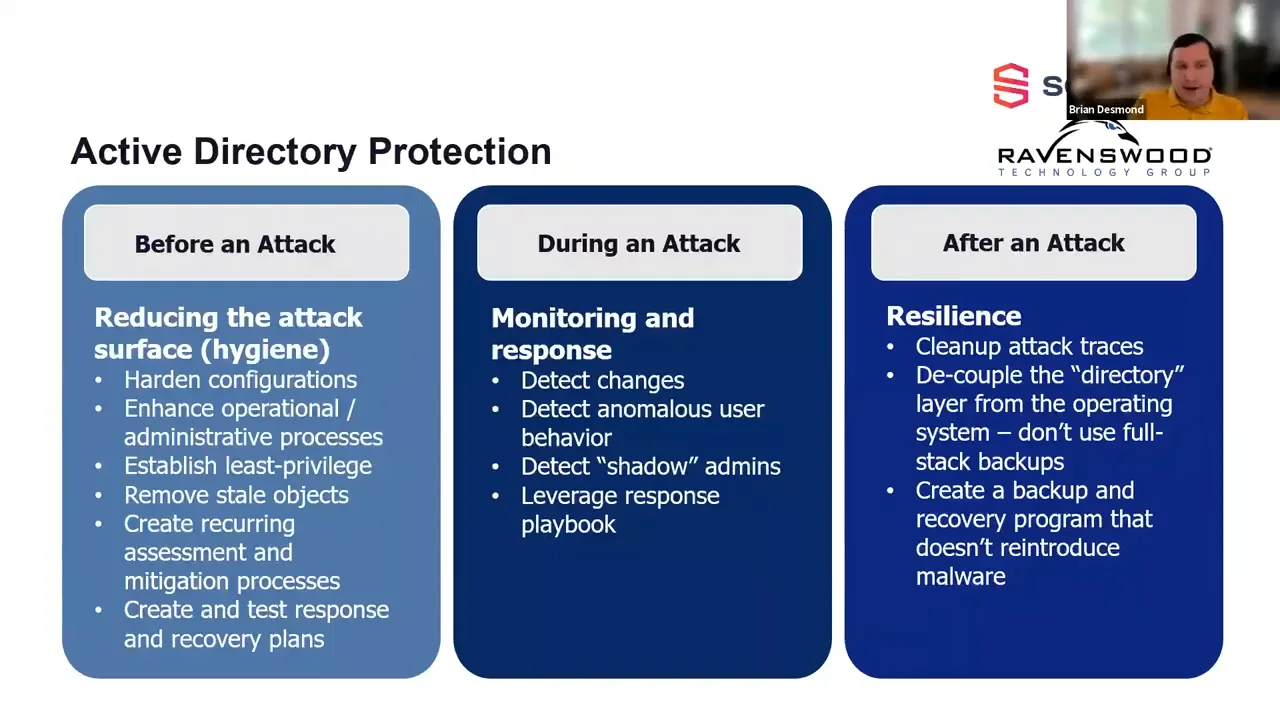
Cyber Forensics - Active Directory Investigation - Cyber Security Blogs - Cyber Forensics - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata