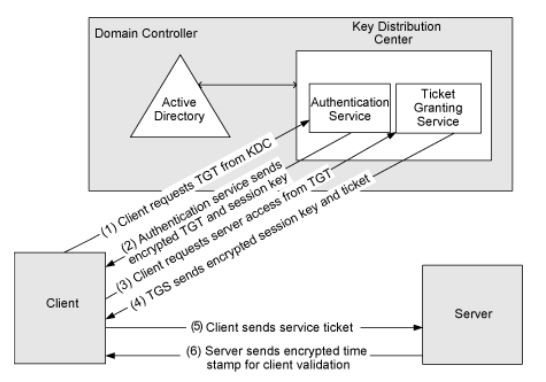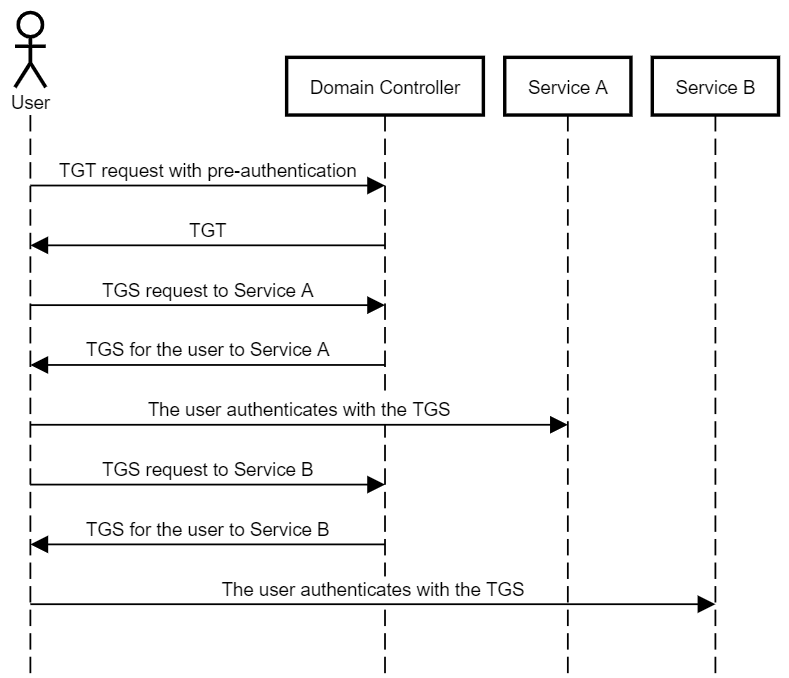
Wagging the Dog: Abusing Resource-Based Constrained Delegation to Attack Active Directory | Shenanigans Labs
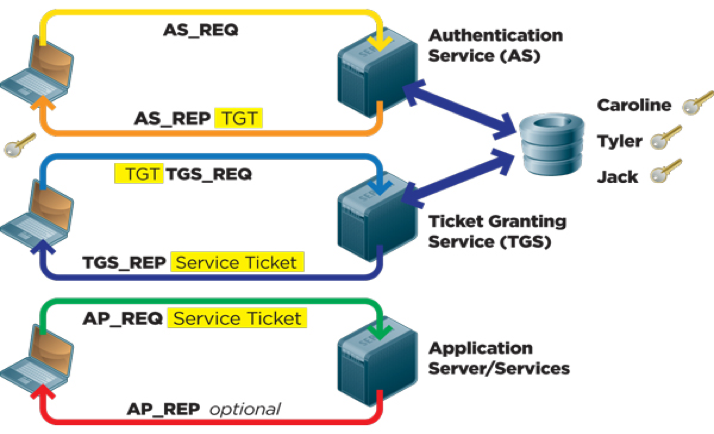
Exploring, Exploiting Active Directory Pen Test - Penetration Testing and CyberSecurity Solution - SecureLayer7

Enabling Single Sign On into SAP using Microsoft proprietary Windows Kerberos authentication(GSS-API) | SAP Blogs

active directory Kerberoasting – Cyber Security Architect | Red/Blue Teaming | Exploit/Malware Analysis